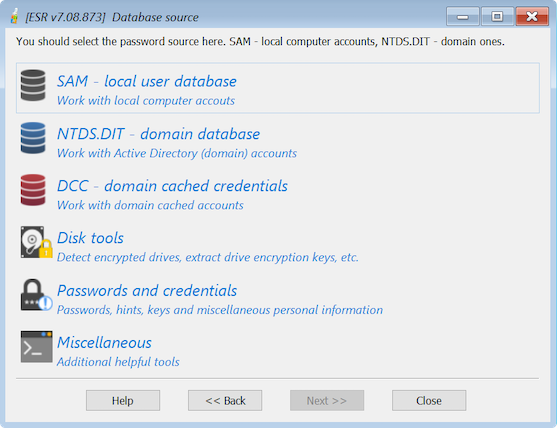
Database source
You can select local and Active Directory accounts. Working with AD requires launching ESR on the server (domain controller) running a Windows Server 2000/2003/2008/2012/2016/2019.
•Work with local computer accounts (SAM)
•Work with Active Directory accounts (ntds.dit)
•Work with domain cached accounts
•Tools to search for disk encryption keys
•Additional utilities
Working mode
•Change account password and properties
•Dump password hashes for further audit/recovery
•Backup Registry or Active Directory to archive
•Restore Registry or AD from backup
•SAM database editor
•Reset DSRM password
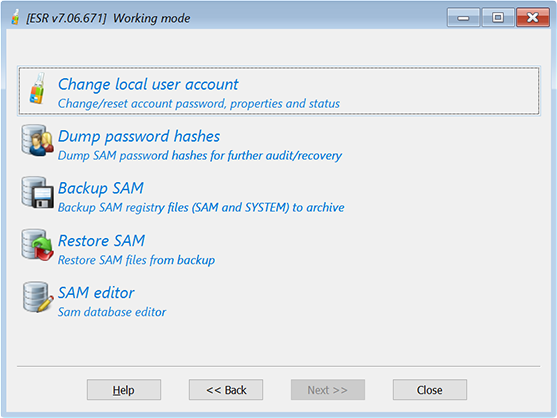
If you already changed some account properties or password(s) and would like to roll back the changes, select the last option: Restore Registry or AD from backup. You will be prompted for locations of a backup copy of the Windows registry or AD database. Otherwise, select Change account password and properties (to change/reset passwords to user accounts, unlock disabled or locked accounts etc), or Dump password hashes... to dump password hashes from the AD or the registry into a text file for further analysis/recovery in Proactive Password Auditor or Elcomsoft Distributed Password Recovery. Finally, you can back up the Registry (SAM, SECURITY and SYSTEM) or Active Directory database (ntds.dit).
When you dump local password hashes from the SAM, password history hashes are also extracted and saved into the dump file.
Password hashes can be saved as a standard dump file in ASCII or UNICODE. After dumping, the program prompts to open the file in Notepad; please note that if the user names or comments use non-US alphabet, they will be shown correctly only in UNICODE.
Finally, SAM database editor allows to edit all the fields in the SAM database that contain advanced properties of local user accounts.