On the main window, specify the following:
•Path to the user keychain file (login.keychain or login.keychain-db)
•User's password (if set)
•Path to the system keychain file
•Path to the system key file
For more information about these files and their locations in macOS, please refer to Obtaining keychain files.
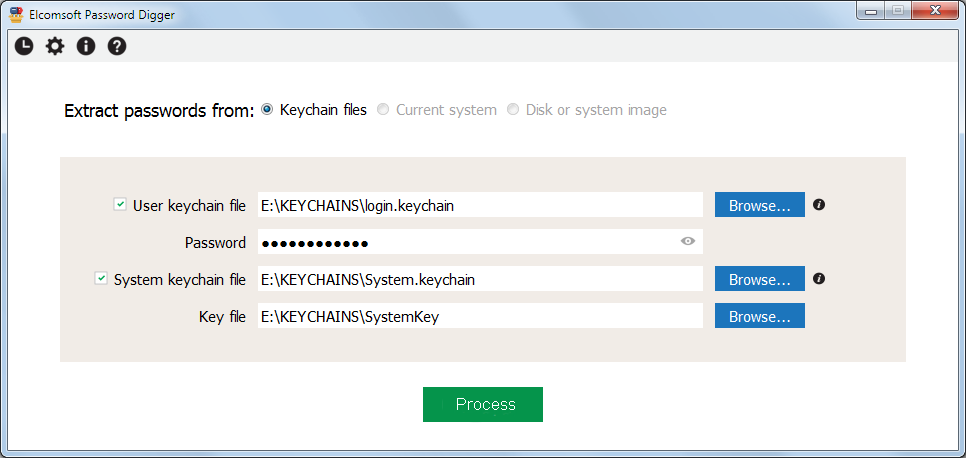
Once the files are selected (you can add user, system or both keychain files), click Process. The next screen shows the number of records processed in each file:
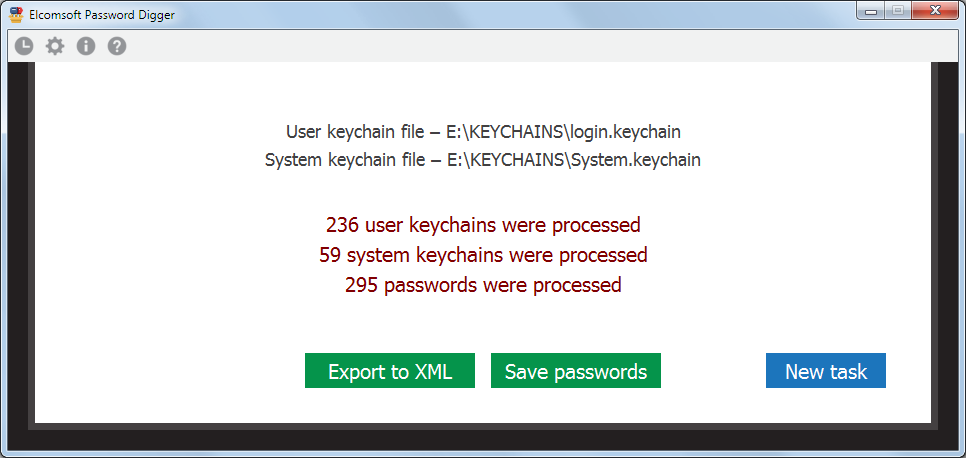
You can export all records into an XML file (suitable for further analysis and/or reporting) or save the passwords into a wordlist suitable for generating a custom dictionary to perform dictionary attacks with tools such as Elcomsoft Distributed Password Recovery. The passwords saved in the file will be deduplicated and sorted. The XML file contains all keychain records including passwords, encryption keys, tokens, and so on, unless you set the "Ignore non-password data in XML output" option.